About the Program
The field of cybersecurity is significantly evolving with a major gap for talents and required skills, both nationally and internationally. The Department of Information and Computer Science is glad to start a new Master of Cybersecurity program to cope with the increasing concerns and needs for competent professionals to address this fast-paced field of cybersecurity. The program is designed to offer a rich complementary curriculum of cybersecurity techniques, tools and technologies to provide graduates with skills needed to proficiently assess threats, analyze vulnerabilities, prevent cyberattacks, protect computer-based assets, ensure privacy, and manage and maintain secure infrastructure systems. Graduates will have attractive opportunities with competitive salaries in numerous jobs including application and system security analysts, consultants, policy makers, and managers.
The high demand of cybersecurity professionals on the job market is significant and growing. Cybersecurity professionals are expected to be very high, as these professionals will create innovative solutions to prevent hackers from stealing or causing problems to computer networks. The U.S. government’s Bureau of Labor and Statistics states (BLS) that the employment of Cybersecurity professionals is projected to grow 32% from 2018 to 2028, much faster than the average for all occupations. In addition, BLS also states that the average pay for Cybersecurity professionals is one of the highest pays among all occupations. An added value to Cybersecurity professionals is job satisfaction. Cybersecurity professionals make a significant contribution to the well-being of their workplace. These professionals are knowledgeable and skilled and understand the importance of securing data and technological systems in the workplace.
Program Educational Objectives
- PEO 1: Established themselves as professionals who can both lead cybersecurity teams as well as be an active member of cybersecurity teams
- PEO 2: Demonstrated an ability to pursue a successful cybersecurity professional and career growth
- PEO 3: Be responsible, ethically driven, and productive members of the cybersecurity professional society
Why Should You Apply?
- The program is designed in line with the best practices of prominent universities offering similar programs.
- The program is designed to offer a rich complementary curriculum consisting of courses from different disciplines that cover cybersecurity techniques, tools and technologies.
- The program aims to produce graduates who will establish themselves as professionals leading cybersecurity teams as well as be an active member of cybersecurity teams.
- The program aims to produce productive and ethically driven graduates to pursue a successful professional and career growth in Cybersecurity.
Program Requirement:
- Applicants must have a bachelor's degree in computer science, software engineering, computer engineering, information technology, information systems, or a related discipline.
- Applicants with bachelor's degrees outside the specified areas must demonstrate significant competence in computer programming, algorithms, computer systems, networking, and operating systems (through academic courses, professional certificates, or taking deficiency courses before joining the program).
Duration: 2 years
Delivery Mode: In-Person
Degree Plan
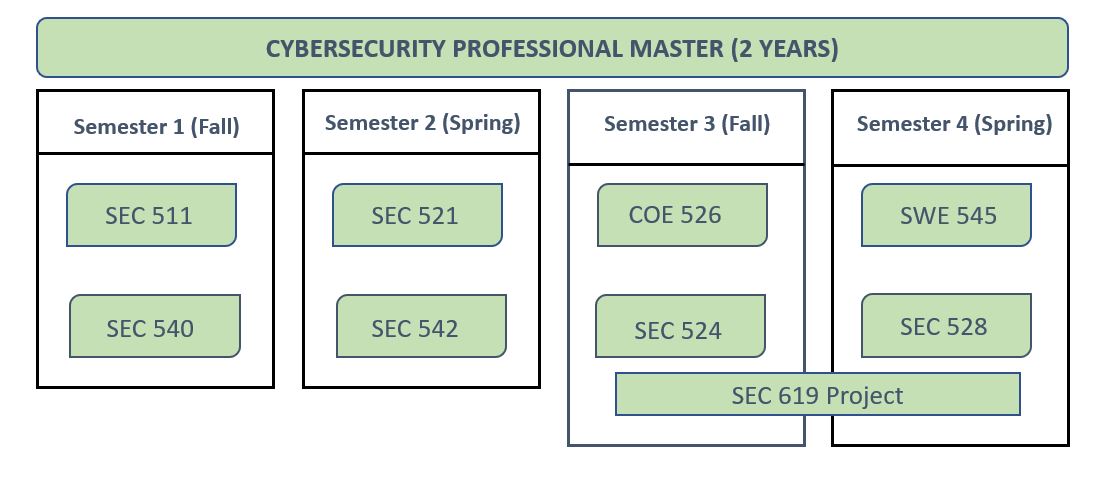
Courses description